Simulate a real threat using the EICAR test file.
1. Check Protection Status
Check we have real time protection enabled before attempting to simulate a threat.
1.1 User Activity
Check real time protection is enabled
Check real time protection is enabled
1
mdatp health | grep real_time1.1 Background Activity
Example output
real_time_protection_enabled is true and managed from the preference file.
1
2
3
4
[labmin@centos-01 ~]$ mdatp health | grep real_time
real_time_protection_enabled : true [managed]
real_time_protection_available : true
real_time_protection_subsystem : "fanotify"1.2 User Activity
Optional: Enable Real Time Protection
Enable Real Time Protection
1
mdatp config real-time-protection --value enabled1.2 Background Activity
Example output
real_time_protection_enabled is true.
1
2
3
4
[labmin@centos-01 ~]$ mdatp health | grep real_time
real_time_protection_enabled : true
real_time_protection_available : true
real_time_protection_subsystem : "fanotify"End Section 1 - Check Protection Status
2. Simulate a Threat
Simulate a threat.
2.1 User Activity
Simulate a threat
We can use a test file to simulate a threat. The EICAR test file is a harmless file that is detected as malware by antivirus software.
1
curl -o /tmp/eicar.com.txt https://www.eicar.org/download/eicar.com.txt2.1 Background Activity
Sample output
The eicar.com.txt file we have been prevented by mdatp
No eicar.com.txt file is present in the current directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
[labmin@centos-01 ~]$ curl -o /tmp/eicar.com.txt https://www.eicar.org/download/eicar.com.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 68 100 68 0 0 68 0 0:00:01 --:--:-- 0:00:01 68
[labmin@centos-01 ~]$ ls -la
total 128
drwx------. 7 labmin labmin 4096 Oct 24 20:55 .
drwxr-xr-x. 5 root root 57 Oct 10 17:42 ..
-rw-------. 1 labmin labmin 4772 Oct 25 23:18 .bash_history
-rw-r--r--. 1 labmin labmin 18 Jul 27 2021 .bash_logout
-rw-r--r--. 1 labmin labmin 141 Jul 27 2021 .bash_profile
-rw-r--r--. 1 labmin labmin 376 Jul 27 2021 .bashrc
drwx------. 3 labmin labmin 20 Aug 31 21:51 .config
drwxrwxr-x. 3 labmin labmin 30 Sep 28 17:41 etc
-rw-r--r--. 1 root mdatp 95 Sep 28 17:14 hot_event_source_1a1767f9-a135-40ec-8286-fc289623d0d4.json
-rw-rw-r--. 1 labmin labmin 0 Sep 13 17:48 installon.log
-rw-------. 1 labmin labmin 61 Sep 28 21:25 .lesshst
-rw-r--r--. 1 root root 91109 Aug 12 2021 libxcrypt-compat-4.4.18-3.el9.x86_64.rpm
drwx------. 2 labmin labmin 29 Aug 23 22:10 .ssh
drwxrwxr-x. 4 labmin labmin 28 Sep 28 17:42 unzip
drwxrwxr-x. 4 labmin labmin 28 Sep 28 17:41 var
-rw-------. 1 labmin labmin 1879 Oct 24 20:55 .viminfoEnd Section 2 - Simulate a Threat
3. Review the Threat
3.1 User Activity
View Threat Details: CLI
We can check MDATP for threats using the following command.
1
mdatp threat list3.1 Background Activity
Sample output
1
2
3
4
5
6
[labmin@centos-01 ~]$ mdatp threat list
Id: "ca6161a5-e76b-46e6-8959-17b08e1a8b76"
Name: Virus:DOS/EICAR_Test_File
Type: "virus"
Detection time: Mon Oct 30 18:16:08 2023
Status: "quarantined"3.2 User Activity
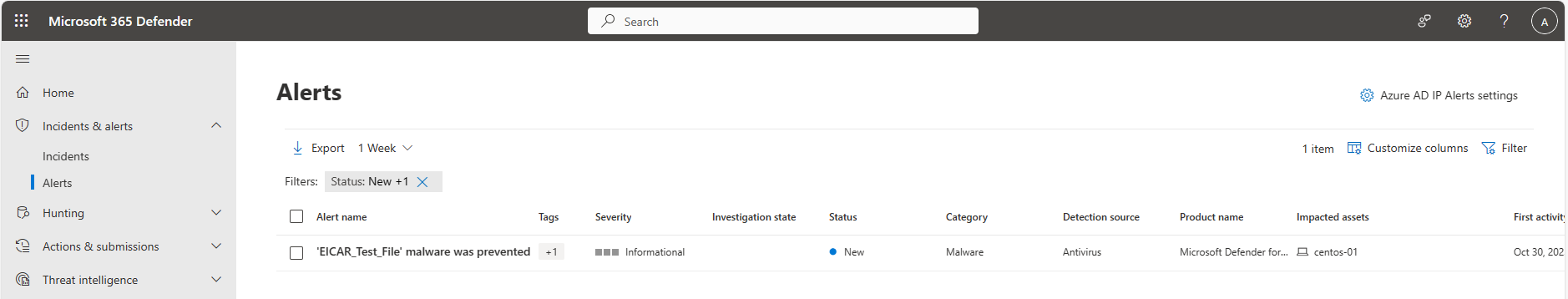
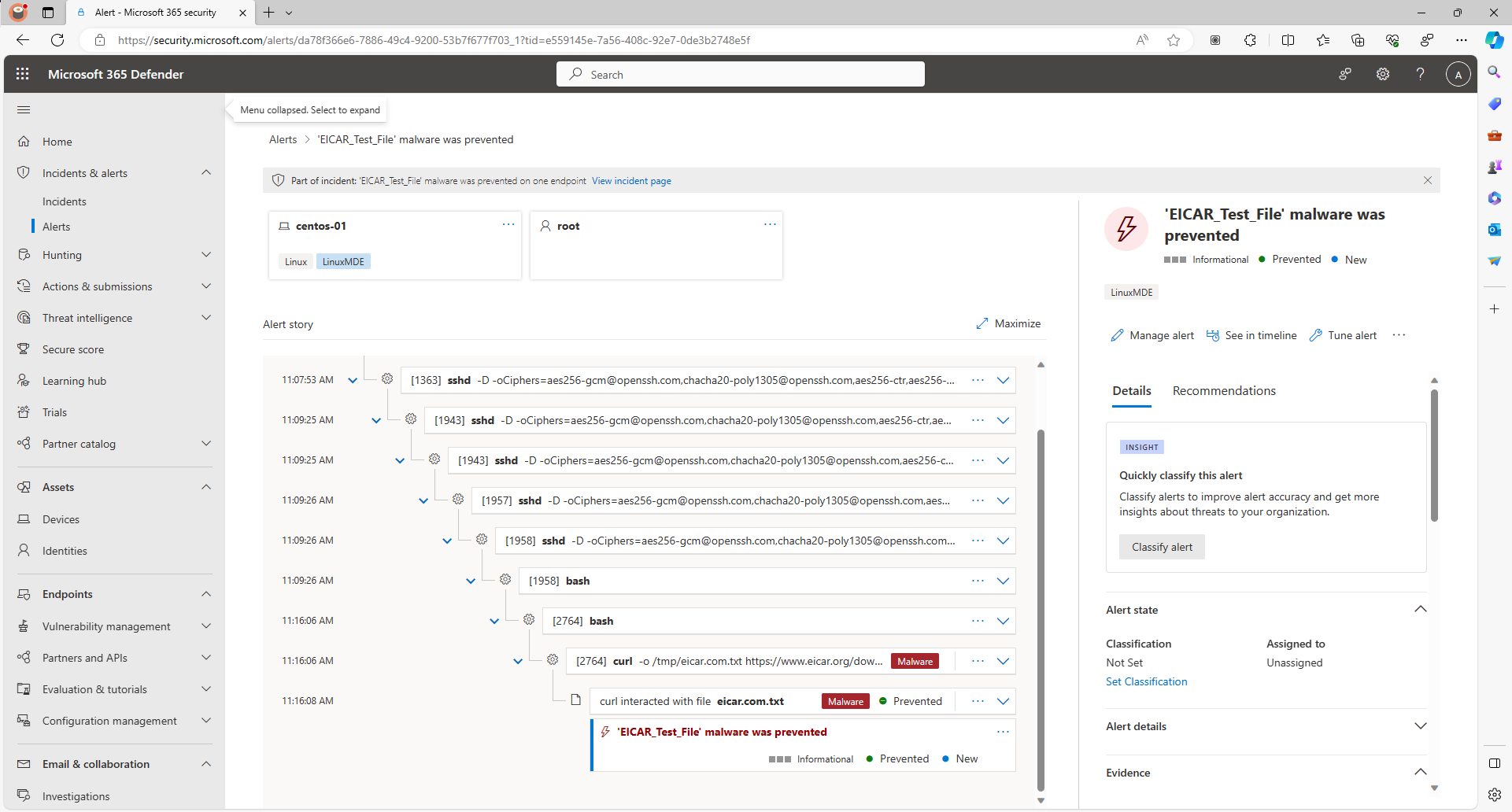
View Threat Details: Microsoft Defender Portal
We can check Microsoft 365 Defender portal for alerts in the Incidents & Alerts pane.
3.3 User Activity
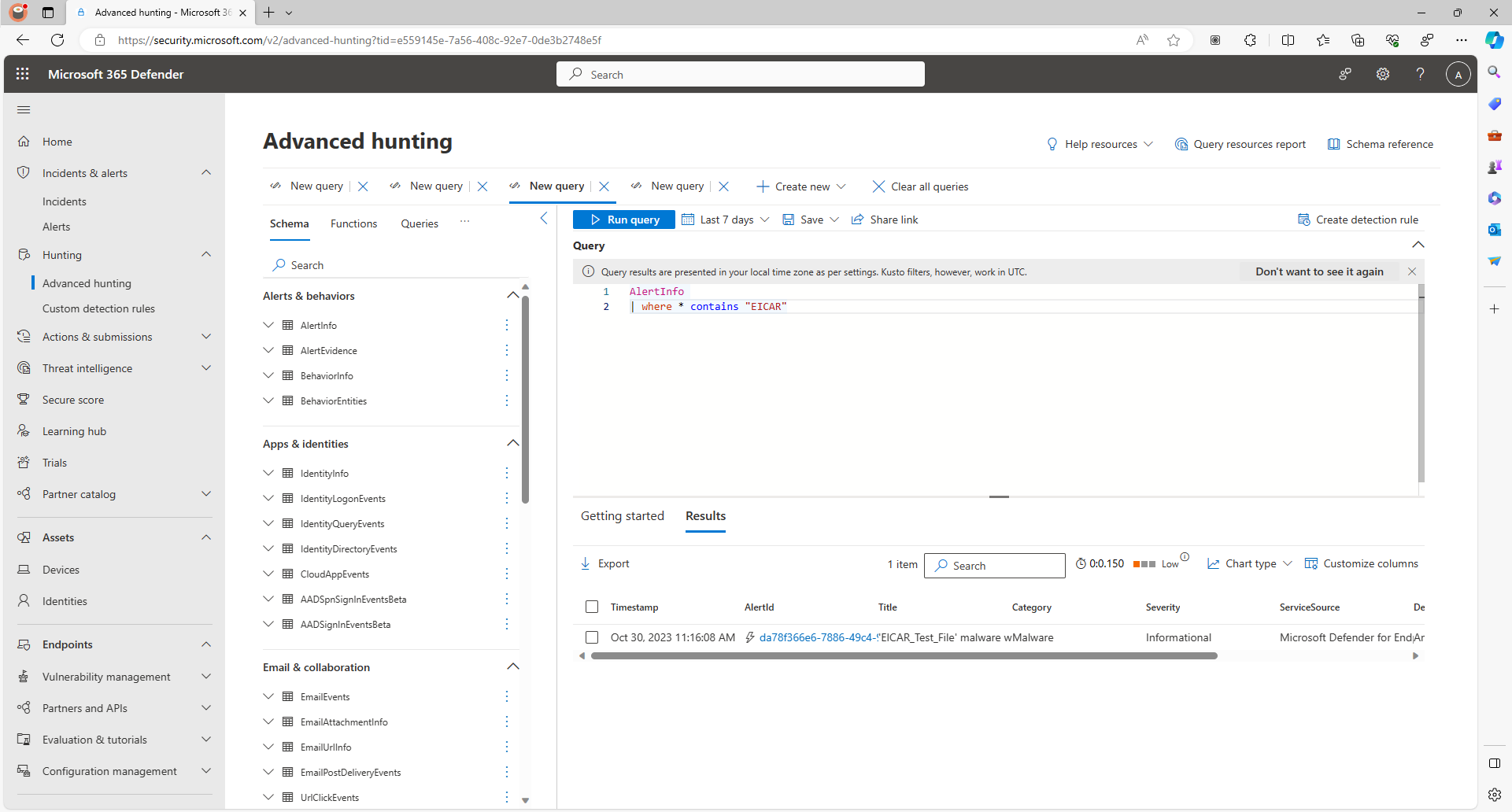
View Threat Details: Microsoft Defender Portal Advanced Hunting
We can check Microsoft 365 Defender portal for alerts using an Advanced Hunting KQL query.
1
2
AlertInfo
| where * contains "EICAR"3.3 Background Activity
Sample output
End Section 3 - Review the Threat